Table of Contents
- 6.1. Enabling Security
- 6.2. Disabling Security
- 6.3. Creating Suitable Certificates
- 6.4. Installing from a Staging Host with Custom Certificates
- 6.5. Installing via INI File with Custom Certificates
- 6.6. Installing via INI File with CA-Signed Certificates
- 6.7. Replacing the JGroups Certificate from a Staging Directory
- 6.8. Replacing the TLS Certificate from a Staging Directory
- 6.9. Removing TLS Encryption from a Staging Directory
- 6.10. Enabling Tungsten<>Database Security
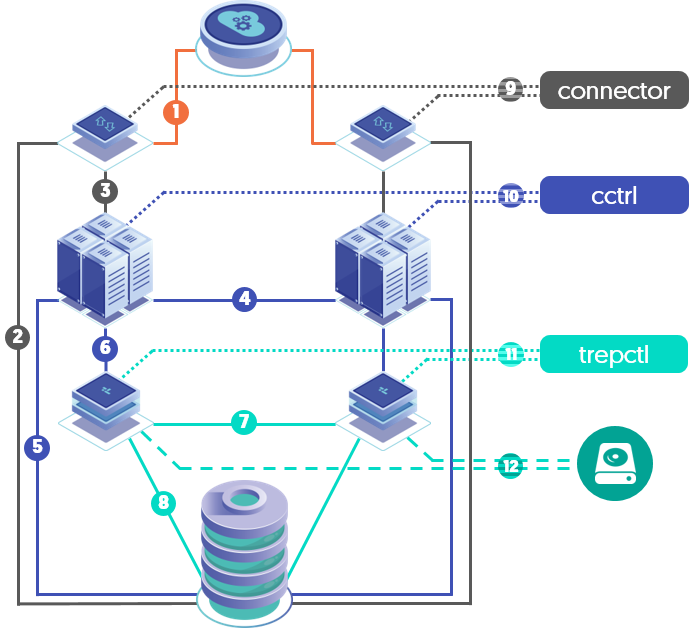
Authentication between command-line tools (trepctl), and between background services.
SSL/TLS between command-line tools and background services.
SSL/TLS between Tungsten Replicator and datasources.
SSL for all API calls.
File permissions and access by all components.
The following graphic provides a visual representation of the various communication channels which may be encrypted.
For the key to the above diagram, please see Section 9.5.18, “tpm report Command”.
If you are using a single staging directory to handle your complete installation, tpm will automatically create the necessary certificates for you. If you are using an INI based installation, then the installation process will create the certificates for you, however you will need to manually sync them between hosts prior to starting the various components.
It is assumed that your underlying database has SSL enabled and the certificates are available. If you need, and want, this level of security enabling, you can refer to Section 6.10.1, “Enabling Database SSL” for the steps required.
Additionally, if you are configuring heterogeneous replication there will additional manual steps required to ensure SSL communication to you chosen target database.
Important
Due to a known issue in earlier Java revisions that may cause performance degradation with client connections, it is strongly advised that you ensure your Java version is one of the following MINIMUM releases before enabling SSL:
- Oracle JRE 8 Build 261
- OpenJDK 8 Build 222